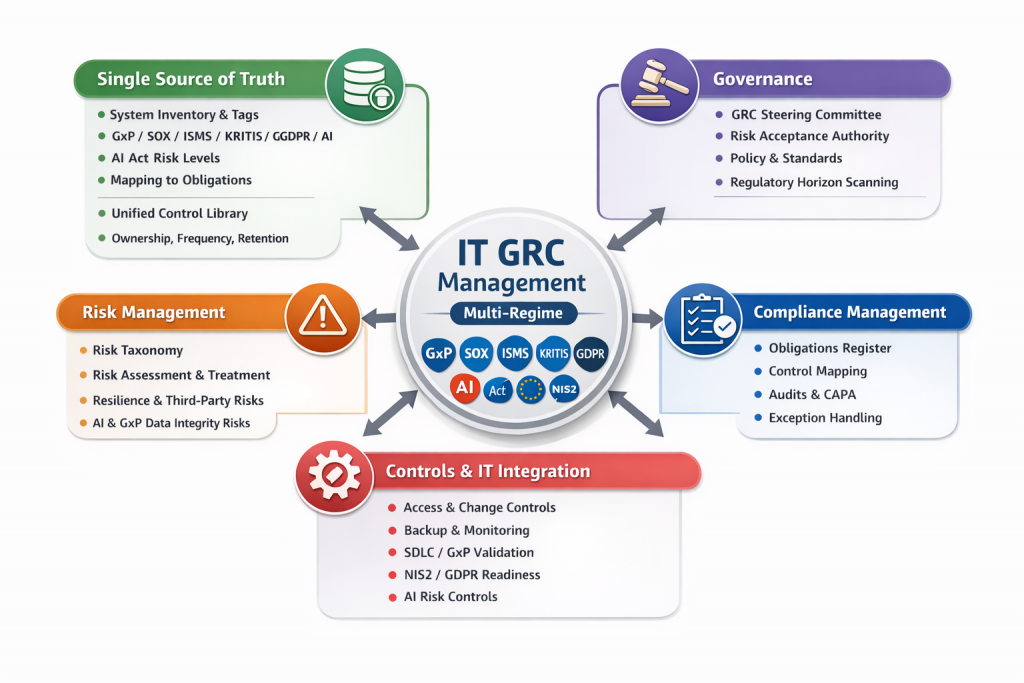
IT GRC Management in Real Life
What IT Leaders Should Actually Focus On (Using the Multi-Regime Mind Map)
If you follow the writing style at Tech & Trust, you already know my position: most GRC pain is not caused by missing frameworks. It is caused by fragmented reality.
Too many lists. Too many spreadsheets. Too many “almost correct” sources of truth. When audit time comes, people start hunting for evidence instead of running a controlled environment.
In this post I want to walk through the IT GRC management mind map in a practical way. Not theory. Not certification language. Just what an executive in charge of IT GRC should really care about when operating across GxP, SOX, ISMS, KRITIS, NIS2, GDPR, and AI obligations.
This connects directly with several ideas already discussed on the blog, especially:
https://techntrust.online/operational-risk-the-blind-spot-of-most-it-teams/
https://techntrust.online/stop-collecting-frameworks-the-practical-it-map-to-iso-nist-cobit-itil-and-gamp/
Let’s go block by block.
The Real Job of IT GRC Leadership
At executive level, IT GRC is not about personally checking controls. It is about building an environment where controls work without heroics.
You are designing a system where:
- decisions are explicit
- risks are visible
- controls have real owners
- evidence is produced by daily work
- audits become verification, not reconstruction
This is very close to the message behind the operational risk article. Most failures are not exotic. They come from how work is actually done every day.
Reference
https://techntrust.online/operational-risk-the-blind-spot-of-most-it-teams/
Single Source of Truth
Start here or you will fight duplicates forever
This is the most underrated part of IT GRC design.
In real organizations, I often see separate lists for GxP systems, SOX systems, security scope, privacy scope, critical services. None fully aligned. All defended by someone. None fully trusted.
A strong model has:
- one system inventory
- mandatory classification tags
- one control library
- one evidence ownership model
Each system gets tags like GxP impact, SOX relevance, critical service, personal data, AI usage. From that single dataset you generate multiple regulatory views.
This is exactly aligned with the idea from your post about not collecting frameworks but building a practical IT map. One map. Many interpretations.
Best starting structures if you need a baseline:
- ISO 27001 control domains
- COBIT control objectives
Governance
Make decisions visible, not implied
Governance only feels abstract until something goes wrong. Then everyone asks who approved the risk, the exception, the shortcut.
Good governance is concrete:
- who can accept which risk level
- who approves exceptions
- which forum reviews top risks
- how policies connect to standards and procedures
If risk acceptance happens in chat messages and hallway talks, you do not have governance. You have improvisation.
What works in practice:
- small GRC steering forum with authority
- written risk acceptance limits
- mandatory expiration dates on accepted risks
- quarterly risk review with leadership
This also connects with your leadership tone in posts that discuss practical governance behavior instead of framework worship.
Useful starting points if someone needs structure:
- COBIT for governance and management split
- ISO 38500 for board level IT governance thinking
Risk Management
If nobody acts on it, it is not risk management
Many teams are very good at producing risk registers. Fewer are good at using them.
Risk management only works when risk information changes decisions. Budget. Priority. Architecture. Sequencing.
A working risk setup includes:
- shared risk taxonomy
- consistent scoring model
- named risk owners
- linked controls
- tracked treatments
In multi regime environments, risk is not only cyber. It includes:
- operational failure
- data integrity breakdown
- supplier dependency
- financial reporting exposure
- resilience gaps
- AI misuse and model risk
This is again directly aligned with your operational risk article. The silent operational weaknesses usually hurt more than the visible threats.
Reference
https://techntrust.online/operational-risk-the-blind-spot-of-most-it-teams/
Good baseline references:
- ISO 31000 for risk lifecycle
- NIST RMF for system level risk handling
Compliance Management
Translate obligations into controls and proof
A question I try to eliminate is “are we compliant?”
The better question is “which controls prove it, and where is the evidence?”
Compliance becomes manageable when you build a simple chain:
obligation → control → evidence → owner
Across GxP, SOX, ISMS, NIS2, GDPR, AI rules, the winning move is reuse. One strong access control supports multiple regimes. One disciplined change process supports several obligations.
Key elements that matter:
- central obligations register
- control mapping
- exception workflow
- audit response model
- remediation and CAPA tracking
This ties very well with your audit readiness positioning across the blog. Readiness is not a pre audit sprint. It is an operating condition.
Reference
https://techntrust.online/operational-risk-the-blind-spot-of-most-it-teams/
Starting references people can use:
- ISO 27001 for ISMS structure
- SOX ICFR concepts for financial controls
- NIS2 guidance for critical services
- GDPR accountability principles
Controls and IT Integration
Controls must live inside IT work
This is where GRC either becomes real or becomes theater.
Controls are not GRC tool records. They are IT behaviors supported by process and tooling.
Focus on a small but strong control set:
- access and segregation of duties
- change and release governance
- backup and restore testing
- logging and monitoring
- configuration baselines
- SDLC and validation discipline
- supplier controls
- resilience and DR exercises
This connects closely with your post about identifying GxP critical IT systems without overengineering. Scope discipline matters more than control volume.
Reference
https://techntrust.online/how-to-identify-gxp-critical-it-systems-without-overengineering/
Solid starting frameworks:
- ITIL for process control integration
- GAMP 5 for risk based validation
- ISO 27001 Annex A for control domains
A Simple Operating Rhythm That Works
Instead of big yearly waves, use steady cadence.
Monthly
Control health and overdue evidence review
Quarterly
Risk acceptance and access recertification review
Semi annual
Resilience and DR exercises for critical services
Annual
Internal audit and management review
This supports the same message repeated across Tech and Trust. Good GRC is continuous, not seasonal.
Final Thought
Strong IT GRC is usually quiet. No drama. No last minute evidence hunts. No control surprises.
When your inventory is clean, your controls are owned, your risks are visible, and your evidence flows from daily work, audits become normal conversations.
That is where compliance turns into trust.