
Stop Collecting Frameworks: The Practical IT Map to ISO, NIST, COBIT, ITIL, and GAMP
Most “compliance chaos” happens because teams mix frameworks without a clear purpose—so the fastest win is to understand what each framework is for, and apply it to the right problem.
The familiar moment when everything becomes “compliance”
A new requirement lands on your desk.
Sometimes it’s from Security. Sometimes from Quality. Sometimes from a customer audit.
The message is always similar: “We need to be compliant with X.”
Then the next meeting happens.
Someone says ISO. Someone says NIST. Someone says ITIL.
A consultant mentions COBIT. A QA lead asks about GAMP.
Everyone nods. Nobody aligns.
A month later, you have templates, policies, and checklists—but still no shared understanding of what you’re trying to achieve. If this sounds familiar, it’s the same pattern that turns audit readiness into a last-minute project instead of an operational state.
The misconception (what most teams believe)
“Framework adoption = compliance.”
It’s attractive because frameworks feel like certainty:
- A named standard
- A list of controls
- A structure you can copy/paste into policies
But frameworks are not compliance by themselves.
They’re lenses. Each one helps with a different kind of problem.
When you treat them like interchangeable “compliance labels,” you create more work and less control.
The operational reality (what actually happens)
- Teams adopt multiple frameworks because different stakeholders ask for different ones.
- Controls get duplicated with different names, and nobody knows which is “the real one.”
- Evidence collection becomes manual and chaotic (“export this, screenshot that”).
- Ownership is fuzzy—frameworks don’t run themselves. People do.
- Over time, compliance becomes a paperwork activity disconnected from operational work.
The cost (what it breaks)
This is how “framework soup” shows up in real outcomes:
- Slower delivery: every change needs extra approvals because the control set is unclear.
- Fragile controls: controls exist on paper but are not integrated into workflows. This is operational risk in its most common form: the gap between documented intent and how work actually happens.
- Audit churn: evidence is recreated every time instead of being produced naturally.
- Hidden risk: the team is busy “being compliant” while real operational gaps remain.
- Fatigue: good engineers disengage when compliance feels like bureaucracy.
The practical fix: a simple model
Use this model to keep frameworks useful and not performative:
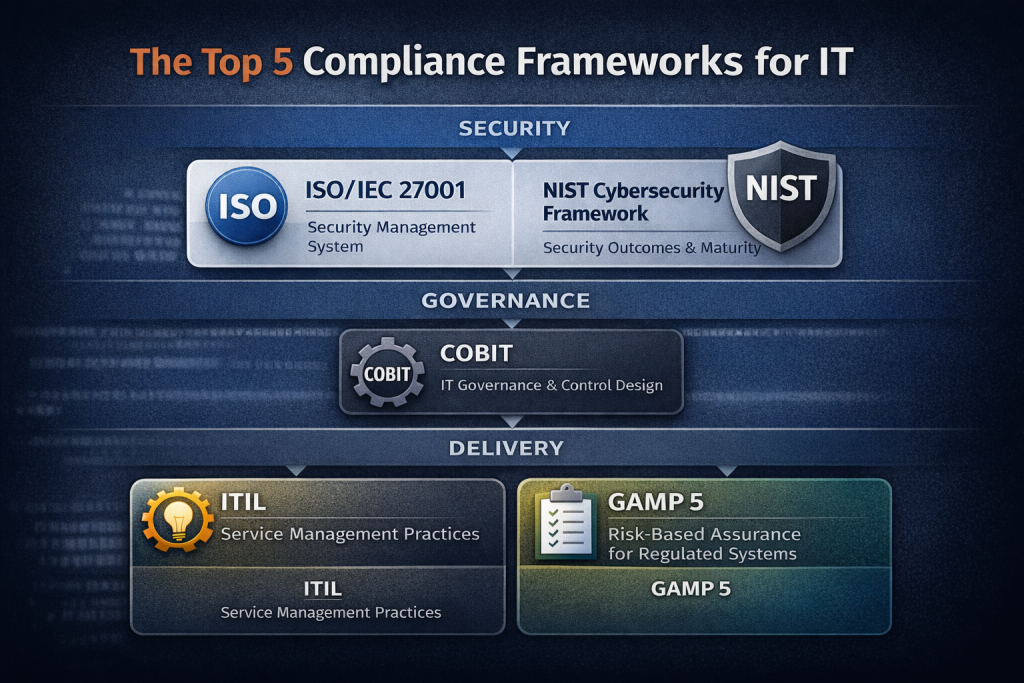
The 3-Layer Framework Model: Security / Governance / Delivery
Layer 1️⃣ — Security baseline (protect the environment)
Frameworks here help you define and run security controls consistently.
- ISO/IEC 27001 (management system for information security)
- NIST CSF (security outcomes organized into practical functions)
Layer 2️⃣ — Governance and control design (align IT to business & risk)
Frameworks here help you define who decides, who owns, and what “good control” looks like.
- COBIT (governance and management objectives for enterprise IT)
Layer 3️⃣ — Delivery and operations (make it work in daily IT)
Frameworks here help you run processes reliably—especially change, incident, and service delivery.
- ITIL (service management practices)
- GAMP 5 (risk-based approach for computerized systems in regulated environments)
The Top 5 Compliance Frameworks Cheat Sheet
1) ISO/IEC 27001 — Security Management System (ISMS)
Purpose: Build a repeatable system to manage information security (policies, risk treatment, internal audits, continual improvement).
Use it when: You need a formal, auditable security management approach—especially across many teams and vendors.
Typical artifacts: ISMS scope, risk register & treatment plan, Statement of Applicability, internal audit plan, management review outputs.
2) NIST Cybersecurity Framework (NIST CSF) — Security Outcomes & Maturity
Purpose: Organize cybersecurity into a practical set of outcomes (Identify, Protect, Detect, Respond, Recover).
Use it when: You want a clear way to explain security posture, prioritize gaps, and show progress without turning it into paperwork.
Typical artifacts: CSF profile (current/target), gap list by function, prioritized roadmap, metrics by domain.
3) COBIT — IT Governance & Control Design
Purpose: Clarify decision rights, accountability, and how controls align to business objectives and risk.
Use it when: Your biggest problem is “who owns what” (controls, risk decisions, exceptions), or when you need a consistent control model across IT.
Typical artifacts: governance map, control objectives, RACI/DRI model, control catalog with ownership, exception handling model.
4) ITIL — Operational Execution (Service Management)
Purpose: Make IT run consistently day-to-day through service management practices (incident, change, problem, SLAs, service catalog).
Use it when: Your controls fail because operations are unstable—frequent firefighting, inconsistent changes, recurring incidents.
Typical artifacts: service catalog, change model (standard/normal/emergency), incident/problem workflows, SLA metrics, PIR template.
5) GAMP 5 — Risk-Based Assurance for Regulated Systems (CSV)
Purpose: Apply risk-based validation so assurance matches system risk and complexity (especially in GxP environments).
Use it when: You operate regulated systems and need defensible validation without validating everything the same way.
Typical artifacts: system classification & risk assessment, validation plan, traceability matrix (as needed), test strategy, periodic review approach.
💡 Now the key: you don’t “simply implement five frameworks.”
You use them to answer five operational questions:
- How do we manage security risk consistently? (ISO/NIST)
- Who owns decisions and controls? (COBIT)
- How do we run IT day to day without chaos? (ITIL)
- How do we validate critical systems without overengineering? (GAMP)
- How do we prove it with evidence that doesn’t collapse under audit pressure? (all of the above—through good design)
What to do this week (actionable checklist)
✅ List your current “framework claims” (what you say you follow) vs. what you actually operate.
✅ Pick one primary framework per layer (Security / Governance / Delivery) and document why.
✅ Assign a DRI (Directly Responsible Individual) for each layer (name + backup). (ownership move)
✅ Identify the top 10 controls you expect auditors/customers to care about (e.g., access, change, backup, incident).
✅ For each control, define where evidence is born (ticket, log, report) and stop accepting “manual evidence hunts.” (evidence move)
✅ Walk one control end-to-end in reality (example: emergency change). Validate the workflow produces evidence automatically. (operational move)
✅ Remove duplicate controls with different names—keep one control definition, multiple mappings.
✅ Create a one-page “Framework Map” that shows which framework supports which layer and who owns it.
✅ Schedule a 45-minute monthly review: “Are controls still operational, or just documented?”
Common traps (so you don’t overengineer)
- Trying to “certify” everything before you’ve stabilized daily operations.
- Writing policies that don’t map to workflows (policies don’t create evidence—systems do).
- Treating framework mapping as the goal (mapping is documentation; control execution is the goal).
- Letting each function create its own control set (Security controls, Quality controls, IT controls… all separate).
- Over-scoping GAMP or validation concepts to systems that aren’t truly critical. A simple risk-based scoping approach prevents validation from becoming a blanket bureaucracy.
- Designing controls that require heroics to run (they will degrade silently).
Conclusion: the one thing to remember
Frameworks are tools, not trophies.
Your job isn’t to “adopt more frameworks.”
Your job is to build a small set of controls that actually run in daily work—and can be proven without panic.
Use frameworks to clarify purpose and ownership.
Then make evidence a natural output of operations.